
The advent of cloud computing has put forth many unforeseen changes. With productivity and profitability spiking to new heights, the world stood in awe as AWS, Azure, and GCP redefined the work culture. With enhanced accessibility and scalability, cloud tech has ushered in a new era in computing.
However, modern-day solutions unwittingly sowed seeds for cloud security solutions challenges. The ease of access has brought unexpected problems. Anyone with the knowledge of the credentials could gain access to the solutions hosted on the cloud.
These aspects have given rise to zero-trust networking. As the name implies, there are no exceptions whatsoever based on trust. It was originally molded to ward off intruders and isolate the cloud application security damage. However, with the growing abuse of access privileges and increasing cyber-attacks, companies relying on cloud security services have adopted zero-trust networking.
Although the emergence of cloud computing security begat the security measure, zero trust is ideal for solutions housed on-premises and on the cloud. The security approach ensures multi-factor authentication for all users, regardless of the user profile and location.
What is Zero Trust?
The security framework of zero trust mandates continuous verification, authorization, and validation of all users, whether inside or outside the company’s network, to ensure proper configuration and posture of the cloud security strategy before granting or maintaining access to applications and data. In the zero-trust model, there is no distinct network edge; instead, networks might be local, cloud-based, hybrid cloud security solutions, or a combination of both, with people and resources distributed around the globe.
The current digital transformation uses the zero-trust framework to secure cloud solutions and cloud infrastructure security. It covers today’s businesses’ contemporary issues, such as protecting against ransomware threats, hybrid cloud security solutions, and remote workers. Reputable organizations have established a range of standards that can assist in aligning zero trust with your organization, despite numerous suppliers attempting to develop their interpretations of the concept.
How Zero Trust Works?

This framework’s implementation combines cutting-edge technologies like robust cloud workload technology, identity protection, risk-based multi-factor authentication, and next-generation endpoint security to verify a user’s or system’s identity. Take current access into account, and maintain system security. Additionally, zero trust calls for considering email security, asset and endpoint hygiene checks, and data encryption before connecting to applications.
Traditional network cloud security strategy, which used the “trust but verified” strategy, has been significantly altered by zero trust. The traditional approach implicitly trusted users and endpoints inside the organization’s perimeter, putting the organization at risk from malicious internal actors and legitimate credentials stolen by malicious actors, allowing compromised and unauthorized accounts wide-reaching access once inside.
Therefore, zero trust architecture requires organizations to constantly check and confirm that users and their devices have the appropriate privileges and attributes. Along with compliance or other requirements to consider before approving the transaction, it also necessitates the implementation of a policy that considers user and device risk. The organization must be aware of its service and privileged accounts to implement controls on what and where they connect. One-time validation is insufficient because threats and user characteristics are constantly evolving.
Therefore, organizations must thoroughly examine every access request before being granted access to any of their corporate or cloud security services assets. Because of this, enforcing zero trust regulations depends on having real-time access to hundreds of users and cloud application security attributes, including:
- Firmware versions
- Installing programs on a device endpoint
- Privileges for credentials on each device
- Authentication risk and protocol
- Operating patch levels and system versions
- Geolocation
- Endpoint function and hardware type
- Identity of the user and kind of credential
- Regular connections between the device and the credential
- Suspicious activity and attack recognition are among the security or event detections
Connecting analytics to trillions of events, extensive corporate telemetry, and threat information is necessary to provide improved algorithmic AI/ML model training for a highly accurate policy response. To contain assaults and lessen the effects if a breach occurs, organizations should carefully examine their IT architecture and potential attack paths. Segmenting by device types, identities, or group functions can be a part of this. For instance, RPC or RDP to the domain controller should constantly be challenged or limited to users with specific permissions.
Using or abusing credentials in the network accounts for over 80% of all attacks. Additional protections for credentials and data are extended to email security and secure web gateway (CASB) providers due to the ongoing development of new attacks against credential and identity stores. The integrity of accounts, adherence to organizational policies, and avoidance of shadow IT services that pose a high risk are all improved by doing this.
Useful link: Debunking Myths Around Zero Trust Security!
Zero Trust Use Cases
In recent years, zero trust has evolved from a widely discussed concept to a formally established approach, primarily in response to safeguarding digital transformation and addressing many complex and severe threats observed in the preceding year.
Zero trust is advantageous for any organization, but yours will start seeing results immediately, provided certain conditions are met. You must secure cloud solutions deployment model for the cloud infrastructure security that incorporates the following:
- SaaS applications
- Unmanaged Devices
- Legacy Systems
- Hybrid, multi-identity, multi-cloud
Zero Trust Principles
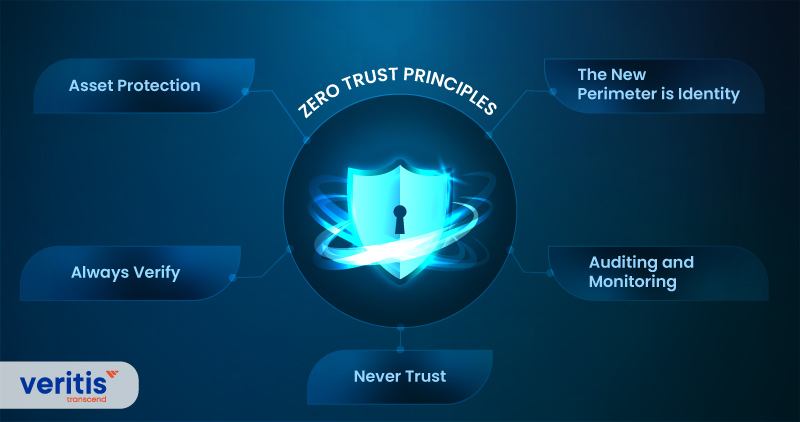
The concept of zero trust relies on five fundamental tenets:
1) Asset Protection
Assets are protected through zero trust, not networks. The zero-trust architecture works under the presumption that attackers would eventually be able to get past the perimeter cloud security strategy. What transpires next is the question. Zero trust technology protects cloud application security and components by requiring ongoing authorization before access, restricting lateral movement, and hiding the network. This keeps organizations and their most valuable assets secure cloud solutions even after a hack.
2) Always Verify
All users and devices are validated and continually authenticated before being given access to any apps or systems. In addition, measures such as single sign-on (SSO) or multi-factor authentication (MFA) give additional protection to the login process and prevent unauthorized devices from accessing sensitive data.
3) Never Trust
Zero trust is only to trust any person or device after they have been authenticated. Building confidence and granting access takes more than the originating network or source. This stops hackers who have compromised the system from accessing crucial information.
4) Auditing and Monitoring
Zero trust enables security teams to monitor and manage any user remotely. They may view logins, user locations, application activity, access logs, and more precisely. In addition, post-incident investigations are made possible by session recordings and complete audit trails, which also assist with regulatory compliance.
5) The New Perimeter is Identity
The ancient perimeter security architecture exposes networks to risk by granting unauthorized access to everyone on the network, including hackers. User and device identities are crucial in a zero-trust environment and must be continuously checked whenever access is requested.
Useful link: What is Security as a Service (SECaaS)?
Thanks to zero trust, companies can now control access and monitor the usage of resources. As being safe than sorry is the new norm of cloud computing security, let’s look at what zero-trust networking is all about.
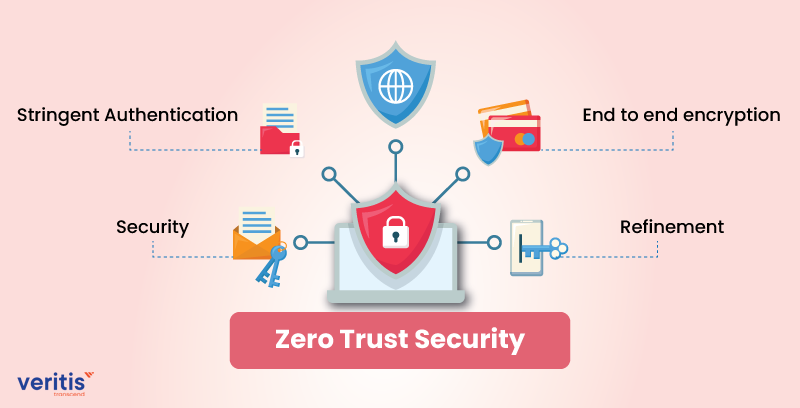
1) Security
Zero trust doesn’t mean distrust, but it implies everyone is subjected to the same scrutiny, irrespective of their roles and responsibilities. The tactical strategy employs multi-factor authentication (MFA), which means one lock would need a minimum of two keys to unlock.
With a primary password decided by the user and a dynamic password provided at the login time, a company can breathe easily as MFA provides better protection to enterprise assets.
2) Stringent Authentication
Zero trust policy restricts the user’s access to enterprise resources based on the login location. For instance, a company can provide access grants to employees only if they are on the organization’s virtual private or in-house network. In addition, this authentication offers no room for unauthorized access, thereby preventing threats from seeping in.
3) End-to-End Encryption
Encryption is vital for any organization to survive. Not only does it stop criminals, but it also keeps the company’s proprietary information from getting leaked. Therefore, employing a robust encryption client and having them set up on all devices across the organization should be a priority.
4) Refinement
Equipping the organization with MFA security and encryption are some shared zero-trust approaches. You should perceive vulnerabilities in your business sector and create a zero-trust strategy that suits you. Additionally, you should keep the strategy current by enhancing it as and when required. This aspect is the cornerstone of your strategy.
However, hammering out a sound zero-trust strategy for emerging security trends can be arduous. Cloud security services providers such as Veritis can alleviate your burden. The third-party service provider will assess the business requirements and tender an adaptable and responsive zero-trust strategy.
Although traditional security is still in vogue, a zero-trust strategy is favored by companies for various reasons. Zero trust has the edge over traditional security because every user has to jump through the prescribed hoops. No exceptions and no loopholes. Thanks to this approach, there is never a question of an employee ever compromising the organization, intentionally or unintentionally.
Should an employee ever decide to go rogue, his conventional efforts would go in vain as the zero-trust approach would nip such efforts in the budding itself. Additionally, traditional cloud security strategy is being swooped to obsolescence as the world ascends to cloud security solutions.
Conclusion
Organizations should realize that there is no such thing as a common strategy for anyone. Every zero-trust strategy is unique as the approach and implementation are defined by the company’s business requirements. And after getting the strategy sculpted, one has to ensure that strategy stays competitive with the ever-changing world.
It is wise to harness the expertise of Veritis, the Stevie Award winner, for we are a formidable force in the cloud realm. With our in-house cloud experts, walk away with a solution customized just for you. Reach out to us and walk away with a zero-trust solution.
More Articles:
- Top 8 Cloud Trends to Watch in 2021 and Beyond
- Top 5 Reasons for Cloud Migration Failure!
- Things to Consider Before Tailoring an Optimal AWS Cloud Strategy
- How to Plan an Effective Cloud Disaster Recovery Strategy?
- A Know-How of Cloud Migration: Azure and Its 4-Step Strategy
- Best Practices that Lead to Good Cloud Governance
- AWS vs Azure vs GCP: Breakdown of Cloud Migration Services
